Electronic Vending Locks
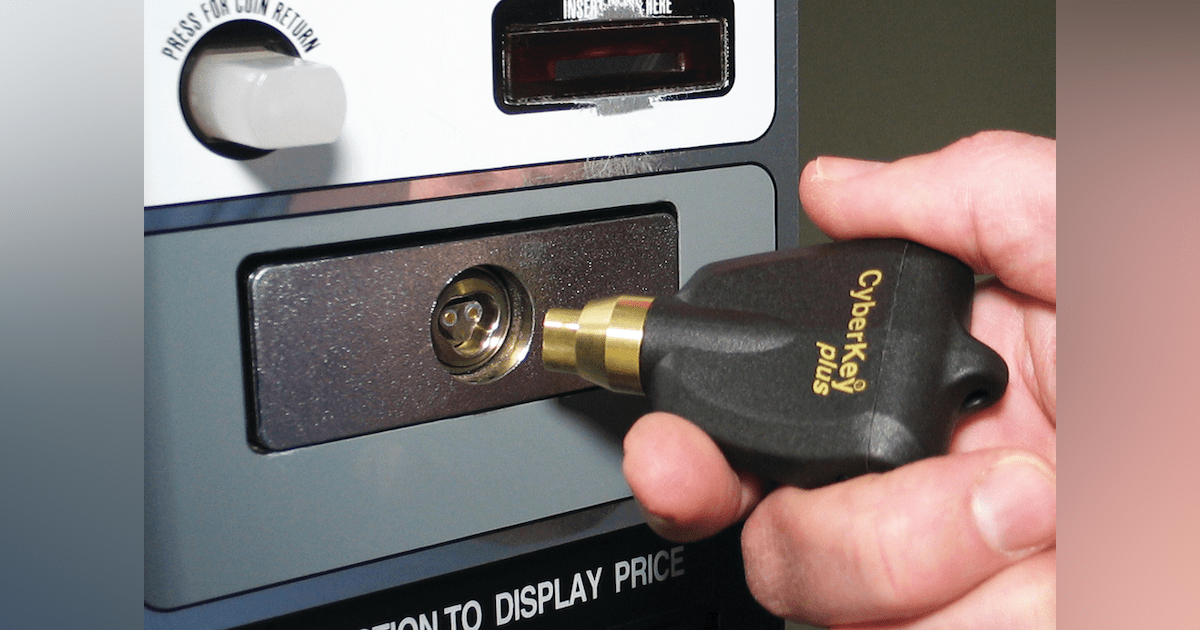
Why would you need Electronic Locks to secure vending machines? After all, vending started out as a penny business and in some ways still is, with razor thin margins. Vending machines are now capable of accepting high denomination bills and credit cards and there are many thousands of dollars of electronics that need protection. So, with protecting the money and margins, electronic locks for vending machines have arrived.
The vending lock cylinder itself is rather small about 2″ long by ¾” in diameter. To make an electronic lock successful it had to be made the same size as the mechanical lock so that it would fit into the millions of machines already in the marketplace.
The power to make the lock function has to come from the specially made electronic key. This is because there are not wires attached to the lock itself. The key has a rechargeable battery that powers the lock when they contact each other. The key also collects audit information from the lock such as the dates and times that it was opened and who opened it. This information is then downloaded at the end of the day into specially written route software. The key can be programmed to only work within certain times of day and if a key is lost it can be blacklisted so it will no longer open any machines.
Features of Electronic Vending Locks:
- Constructed of stainless steel with a steel locking bolt
- Drill and tamper resistant lock cylinder
- For Indoor or outdoor locations and is weather resistant
- Designed to replace current mechanical locks
- All power to be supplied by the key
- All programming is done at the key and transferred to the lock
- Software can be stand alone, network, web and mobile programming
- Rechargeable battery in the key
The software is capable of being stand alone, network or web based. Within the software the administrator can set up authorized users, routes and timed entry in the machines. The information collected from the locks is downloaded into the software when the key is being recharged. This information shows what time of the day the machine was opened, how long it remained opened and who opened it. It also records unauthorized attempts to open it. If a key is lost the software can remove that key from the system. There is also the option of mobile programming by using a smartphone, so that the key programming can be changed anytime during the day.





